Brand impersonation (or brand spoofing) is a form of phishing and social engineering in which the fraudster poses as a legitimate brand. A brand impersonation attack leverages consumer trust in the brand to trick the target into divulging personal or otherwise sensitive information like credit card numbers, social security numbers, and login credentials. Fraudsters will also impersonate well known brands in order to engage in non-delivery fraud (charging customers for services or products they have no intention of delivering) or tricking consumers into purchasing counterfeit goods. Such attacks can take the form of phishing emails, SMS messages, social media messages, voice calls, or communications through other channels.
Any brand can be hijacked and used as part of brand impersonation scams. At Allure Security, we see numerous examples of small businesses being targeted by brand impersonation attacks. From a playground equipment manufacturer to a small boutique, fraudsters can leverage the trust in the brand to commit fraud. That said, larger organizations can present a more lucrative target for fraudsters. Large organizations, like Amazon, Microsoft, Apple, and Google, have wider user bases and larger repositories of data to exploit.
Brand impersonation poses a risk for the target because the malware downloaded or personal information revealed can be used to gain access to financial resources and corporate networks or otherwise inconvenience the target. However, brand impersonation also harms the brand that is being used in the attack. Brand impersonation erodes the trust and relationship brands work hard to establish online, ultimately leading to fewer customers and lower revenue as victims gravitate towards more trusted brands.
Brand spoofing continues to be a popular choice for cybercriminals, and the impact of such attacks cannot be understated. In 2023, the Federal Trade Commission received more than 330,000 reports of business impersonation scams as well as nearly 160,000 reports of scams impersonating government agencies. That number represents nearly half of all fraud reported to the FTC. The financial consequences of these attacks tops $1.1 Billion.
This article provides an important overview of brand impersonation, what it does, how it works, and how it can be prevented. Browse our Table of Contents below to quickly navigate the article.
Table of Contents:
How Does Brand Impersonation Work?
Nearly a third of all business is conducted online. Whether that’s e-commerce, streaming, financial services, you name it — individuals typically interact with multiple brands on any one day as a part of everyday life. Fraudsters will exploit these trusted relationships by impersonating brands via scam websites, posing as brand representatives on social media, sending phishing emails, and more. Large brands, small businesses, and companies of all shapes and sizes need to communicate with their customers from time to time. If the customer has an online account or profile, there could be minor issues that require remediation. If the company conducts e-commerce through their site, there could be a need to discuss a recent order. It is a common occurrence, and individuals are often fielding messages with one brand or another as part of everyday life.
Some brand impersonation attacks will exploit this exchange by fabricating an urgent situation that requires immediate support. The target is presented with a crisis with imminent consequences unless they click a link or divulge personal or otherwise sensitive information. They are primed to comply with the request because of the existing relationship the target has with the brand. They’ve communicated before, perhaps over years. That inclination to trust, click, and log in is enough for phishing attacks to fulfill their objective.
When studying brand impersonation and phishing attacks, it may seem easy to recognize fraud. The inconsistencies, unprofessionalism, and thinly-guised malicious links can seem obvious – though generative AI is making it easier for cybercriminals to avoid these telltale signs of deception. Brand impersonation works because it is often perpetrated at scale. Any individual phishing attack may have a success rate of less than 1%, but if conducted a thousand times a day using automation, the number of impacted victims accumulates quickly.
Threat Actors Creating Their Own Link-Shortening Services
With fraudsters developing new techniques to circumvent cybersecurity tools, security professionals need to go on offense. Learn how cybercriminals are using obscure or self-made link-shortening services to obscure malicious URLs.
Types of Brand Impersonation Attacks
There are many types of brand impersonation attacks and many deceptive personas utilized to solicit sensitive information or steal login credentials to gain access to key accounts. Here are some of the most popular:
-
-
- Technical Support: A fraudster can impersonate the technical support team of an organization and use that brand to trick customers. They may, for example, ask customers for login credentials under the guise of resolving a technical issue.
- E-Commerce: E-Commerce sites are popular targets of brand impersonation due to the transactional nature of the website. Users come in to make purchases with their credit card and financial information. Brand impersonators create fake shops or pose as members of the support team who need personal information to resolve issues with a recent order.
- Job Offer: Brand impersonators may pretend to be part of the recruiting team reaching out to potential candidates using fake social media accounts or phishing emails. Job candidates are eager to respond to requests from the organization in the hopes of landing a position. This eagerness is ripe for exploitation.
- Legal Entity: The relationship between legal representation and their clients is a special one that contains an expectation of confidentiality. The brand impersonators use that trust to solicit sensitive information from victims.
- Social Media Brand Spoofing: Social media brand spoofing is when cybercriminals create fake social media accounts to impersonate the social presence of another brand for the purposes of fraud. The fake social media accounts could be used as part of a larger string of impersonation attempts to solicit sensitive information or gain access to important accounts. A common strategy in social media brand spoofing is to impersonate an employee or executive from an organization, especially on Facebook, X/Twitter, and LinkedIn. The fraudster then uses that guise to manipulate its target into divulging sensitive information or to extract wealth.
- Law Enforcement Scam: Though impersonating a law enforcement officer is itself a crime, cybercriminals will still utilize this position of authority to coerce targets into sharing information. They may pose as a local officer or even a federal agent.
- Subscription Scam: In a subscription scam, the fraudster pretends to be the support team of a recognizable subscription service. The fraudster will reach out to the target explaining that they have been accidentally billed for services. To receive a refund, they must input certain sensitive information or login credentials.
- Executive Impersonation: Employees have few motivators stronger than a direct request from an executive at the company. Brand impersonators exploit this dynamic by posing as an executive with an urgent request.
-
For more information on the types of attacks fraudsters are using today, refer to the MITRE ATT&CK framework technique T1656: Impersonation: “Adversaries may impersonate a trusted person or organization in order to persuade and trick a target into performing some action on their behalf.” Cybersecurity professionals use the framework to develop the next generation of security solutions and combat known threats, but any organization can leverage the MITRE ATT&CK framework to educate themselves on brand impersonation, phishing, and fraud strategies. This information can be used to inform internal training and cybersecurity policies.
Brand Impersonation Attack Mediums
Along with different personas, brand impersonators make use of a variety of channels to distribute their phishing messages. Review common mediums below:
-
-
- Mass Email: Email remains a popular attack method for fraudsters because phishing emails can be created cheaply and quickly and then distributed at scale. Further, emails can be easily manipulated to deceive the target. Email domains can be changed, email signatures can be replicated, and links can be hidden. All an impersonator needs to initiate the attack is the target’s email address — something that can be found publicly.
- Phone Calls: A voice phishing (vishing) attack can be performed through an auto-dialer or VoIP system. Vishing has a key advantage over an email attack — many people are uncomfortable in a confrontation. In a vishing call, the target may be susceptible to fear and intimidation. The fraudster may solicit sensitive information from victims in an urgent attempt to solve the problem. A phone scam deprives the target of the ability to think calmly by applying immediate pressure.
- SMS Text Message Scam: Otherwise known as SMishing, this form of phishing is conducted through an SMS message. A SMishing attack will often make use of short links which make it more difficult to determine the destination at a glance.
- Mobile App Marketplaces: Fraudsters will publish altered versions of a brand’s official app on third-party marketplaces. The strategy is to trick users into downloading the application, believing it to be the legitimate app. From there, a fraudster can leverage key loggers, screen scrapers, or other malware to complete their scam.
- Social Media: Especially prevalent on Facebook, LinkedIn, and X/Twitter; attackers will impersonate executives, employees, or the official social account of an organization to perpetrate fraud. Social media provides direct messaging tools that make it easy for fraudsters to connect with their targets and initiate a social engineering scheme.
- Multiple Phishing Methods: Sophisticated attacks may combine multiple forms of phishing into one coordinated attack. Initial phishing emails could provide phone numbers for the target to call. From there, vishing calls can prompt users to click malicious links sent over text that direct the recipient to credential harvesting sites or sites that download malware onto the device.
-
Spoof 2023: Trends in Online Brand Impersonations for Retail, Hospitality & Consumer-Facing Brands
Download comprehensive research on online brand impersonation trends in H1 2023. Within, you’ll learn about which retail segments are prime targets and data proving why older approaches to the problem of brand impersonation are no longer sufficient.
How to Identify Brand Impersonation Scams
The hallmarks of brand impersonation attacks are the same as those found in standard phishing attacks. To illustrate, below we’ve created a fictional example of a brand impersonation email and noted four ways to identify it as such. This is not a comprehensive example and fraudsters are always testing new techniques, but if a message from a known brand contains these elements, it is cause for skepticism.
It is worth noting that brand impersonation messages, whether in email or another channel, are becoming increasingly difficult to identify. These best practices remain valuable, but the increasing sophistication should spur organizations to do more to protect their brand online. Though the organization is not at fault for a cybercriminal hijacking their brand, the consumer is more likely to hold them responsible than the cybercriminal. For that reason, these best practices for identifying a brand impersonation attack should be used in conjunction with online brand protection services.
Example Brand Impersonation Email
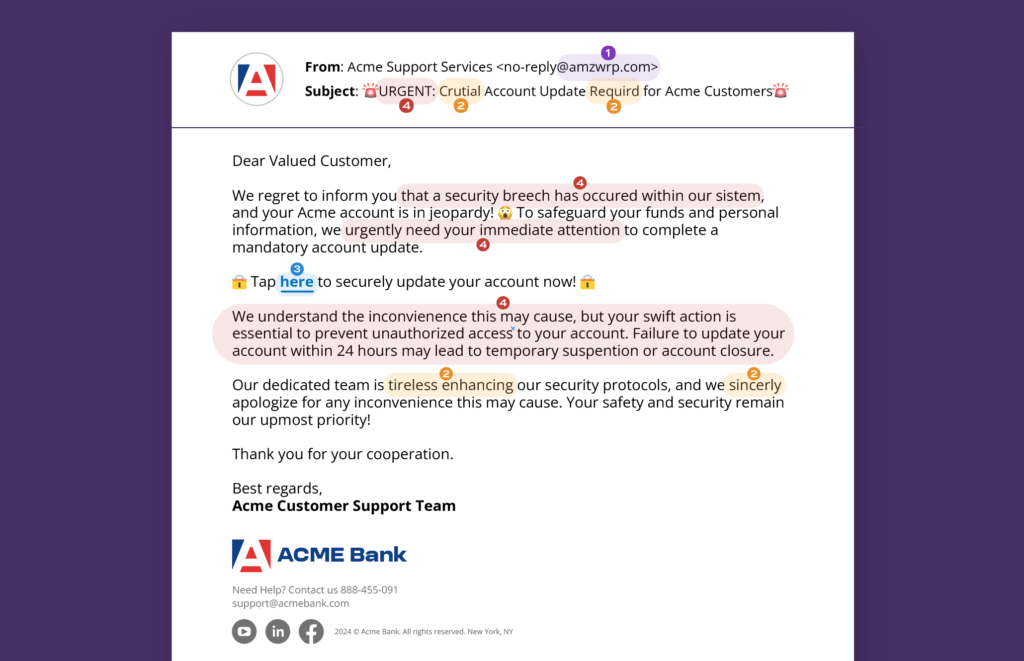
-
-
- Spoofed Display Name: A display name in an email presents an alternative to listing the domain name. The legitimate purpose of a display name is to provide clarity on the identity of the sender when an email address does not do so on its own. For example, a display name of “Allure Security Customer Support” is more obvious to the recipient than “[email protected]”.
A phishing email can exploit the display name tool by creating a display name that has relevance or association with the impersonated brand, even if the email domain is entirely separate. On mobile platforms, the recipient may only see the display name in the interface, making the scam more difficult to spot. Checking the email domain underlying the display name could signal a spoof.
- Spoofed Display Name: A display name in an email presents an alternative to listing the domain name. The legitimate purpose of a display name is to provide clarity on the identity of the sender when an email address does not do so on its own. For example, a display name of “Allure Security Customer Support” is more obvious to the recipient than “[email protected]”.
-
- Misspellings and Grammar: Legitimate brands employ copywriters and editors to ensure a consistent tone and style in their communications. If you receive a message from a brand with misspellings, grammatical errors, or other oddities, it may indicate a brand impersonation attack. Phishing messages often contain these careless mistakes for two reasons. The first is that many are not native English speakers who may not realize their error. The second is that cybercriminals operate at scale and may be writing dozens of these messages at a time. This increases the likelihood of mistakes. However, as discussed below, AI chatbots are making it easier for attackers to avoid spelling and grammar mistakes.
-
- Suspicious Link: Hover the mouse cursor over the link in the email or communication. Most platforms will then display the URL behind the anchor text of the link. If the URL originates from an unexpected domain or otherwise looks suspicious, it probably is. Reconsider clicking on the link and instead contact the provider using a different, official channel.
-
- Sense of Urgency: The most important element of any phishing or brand impersonation scam is a sense of urgency. The fraudster will present a crisis with dire consequences if the target does not act immediately. The crisis could threaten the target professionally, personally, or financially, but the key is that the target themselves must be the one to act.
-
Identifying Other Forms of Brand Impersonation
-
-
- Social Media Spoofing: Fake personas are easy to create on social media. Social media accounts are a marketing distribution channel connected to each part of the brand’s digital footprint. Before responding to a suspicious message, look more closely at the account. Is the profile information complete, accurate, and professional? Does it link to the official website? If on LinkedIn, does the account have many 1st connections with individuals at the organization? Do they have a plausible career history? You could also try a reverse image search of their profile picture to see if the picture is a stock photo or otherwise repurposed from another account.
- SMS Text Messages: Many of the red flags of a smishing message are the same as those found in a phishing email. It may contain suspicious links, grammatical mistakes, an urgent crisis, and so forth. A common smishing strategy is to target a geographical area while impersonating the brand of a local financial institution. This “spray and pray” strategy targets a large pool of recipients knowing that a percentage of that pool is a customer of the financial institution and therefore more likely to click. Verify the authenticity of a smishing message, do not click the link. Instead contact the institution through another channel, like a phone call, and ask the representative to verify the issue.
- Fake Websites: Two effective strategies to verify the authenticity of a website include the URL and researching the site’s history. First, ensure the URL is correct. Second, confirm the age of the website. Major brands should have websites with years or decades of history and revisions. Use a tool like the WayBackMachine to investigate.
-
Before You Click!
Before clicking on any suspicious message, here are two steps an individual can take to investigate its authenticity:
-
-
- Verify the Sender: In some brand impersonation schemes, the fraudster may pose as someone known to the target or from a real department in the organization. Remember, the success of phishing attacks hinge on creating a sense of urgency that prevents the target from thinking the situation through. If, for example, you receive a message from an accounting colleague about an urgent payroll crisis, reach out to someone in the department through a different channel (e.g., Slack or by phone) to confirm the situation and verify the sender.
- Communication Methods: Organizations develop specific policies on how to communicate with customers. This is especially true of financial institutions. If the communication received is in an unexpected channel, it warrants further investigation. For example, many banks will not communicate with customers via direct message over social media, unless it is part of a specific program that the customer has opted-into. Verify that the communication channel is both reasonable and that the company uses this channel for the types of messages in question.
-
How AI Threatens to Exacerbate Brand Impersonation
The potential of AI is just beginning to be revealed, and businesses in every industry are searching for ways to leverage the technology to improve processes and reduce costs. The cybercrime industry is no different.
AI will help cybercriminals overcome some of the limitations in their operating model. Currently, fraudsters produce or repurpose phishing messages at scale which leads to common grammatical mistakes and awkward phrasing. In turn, those grammatical mistakes become one of the best ways to identify a suspicious message. Large language model (LLM) chatbots, like ChatGPT, eliminate that issue for fraudsters. They can create, in a very short amount of time, numerous different phishing messages calibrated for email, social media, SMS, or other mediums with perfect spelling and grammar.
Text is only one threat. AI can generate images as well with surprising realism and near-instant speed. A fraudster could fabricate an album of photographs featuring the same artificial person in different settings to create a more convincing social media spoof. In Hong Kong, a finance worker was deceived into giving a fraudster $25 million after participating in a video conference call with what appeared to other employees at the company. The fraudster used deepfake technology to pose as the chief financial officer during a live video call along with several other deepfaked professionals.
It is unclear what direction cybercriminals will take AI next, but what is certain is that it will become a critical tool in both the execution and prevention of brand impersonation schemes moving forward.
Brand Impersonation Protection
The threat of brand impersonation scams and phishing attacks is a persistent one. The low costs, speed of deployment, and potential return provide ample incentive for more and more brand impersonation. We should not expect impersonation to lose popularity with cybercriminals, but there are brand impersonation protection strategies to reduce the likelihood of customers or employees falling victim.
-
- Register Brand Name and Trademarks: It is important to register any trademarks and brand names with the relevant government agencies. This will provide a pathway in the event that legal action becomes necessary.
-
- Email Signing Certificates: Equip your email communications with an email signing certificate that encrypts your email messages against manipulation. This ensures the customer that the email is legitimate. The absence of a certificate can also be a cue for the recipient to be skeptical of the message.
- Domain-based Message Authentication: There are several tools a brand can make use of to prevent their domain from being spoofed. Set up DomainKeys Identified Mail (DKIM) on your domain name to mitigate unauthorized parties sending emails spoofing your email domain.
- Filter Spam: Many email, text, and voice call platforms provide tools to filter out spam emails, SMS messages, and Vishing calls. Though imperfect, these tools can help weed out a significant portion of phishing messages or raise suspicions about messages with a higher likelihood of being fraudulent. Remember to check the spam folder regularly in case legitimate communications were redirected in error.
- Leverage BIMI and VMCs: Brand indicators of message identification (BIMI) in conjunction with verified mark certificates (VMCs) allow the organization to brand their email communications within recipients’ inboxes. A verified company logo can be embedded into the email to reassure the recipient that the message comes from an authentic source. These verified logos are different from simply adding a PNG to the body of an email. The logo will be located at the inbox view before the email is opened. There are, however, no silver bullets in cybersecurity. There are ways to spoof BIMI and VMCs. This is a helpful tool for protecting your brand, but it is important to leverage multiple overlapping strategies to reduce the threat.
- Monitor External Facing Assets: Cybersecurity solutions providers, like Allure Security, offer online brand protection services and digital risk protection services aimed at preventing brand impersonation attacks. Sophisticated algorithms crawl the organization’s digital footprint to map out all external-facing digital assets, such as websites, social media accounts, partner sites, and more. From there, they can identify spoofs resembling the brand, initiate takedowns, and/or inform the security team of the threat.
- Educate Customers: One way to prevent a successful brand impersonation attack is to educate your customers on the threat. Send out communications by email or whatever channel is most appropriate for the audience, inform them of the threat, and explain what legitimate messages from the brand will look like. If there are channels that will never be used to discuss account-related issues, state that, so the customer can recognize a suspicious message at the outset.
- Educate Employees: In addition to any standard phishing training program, educate your workforce on the various partner relationships the company maintains, what their communications look like, and what to do if a message from a partner appears suspicious. Ultimately, the same strategies an individual uses to identify brand impersonation will apply to suspicious partner communications. Equip your team with a clear protocol should they encounter a suspicious email. The team should know what to do in response and to whom it should be reported.
WHAT YOU SHOULD DO NEXT
Expand your knowledge of phishing and brand impersonation scams with the blog article, “Phishing Kits Targeting Regional Banks and Credit Unions”. In it, we cover how phishing kits make it easy for fraudsters to deceive traditional online brand protection techniques and how anti-bot technology is repurposed by fraudsters to circumvent cybersecurity efforts.




