In the course of monitoring for, investigating, and eradicating online brand impersonations of our customers, we regularly come upon websites that use phishing kits and host multiple phishing pages targeting multiple regional bank and credit union brands and their patrons.
We’ve discovered web pages matching this pattern for years but observed a surge in such credential harvesting campaigns this month. What’s also novel about these particular phishing sites is their use of free bot detection services such as Cloudflare Turnstile.
Threat actors’ use of these bot detection tools has significantly reduced the effectiveness of traditional approaches to online brand protection including those of some brand protection vendors.
With this article we hope to make regional banks and credit unions aware of the increasing prevalence of these phishing websites and explain why traditional online brand protection or threat intel-based approaches to these phishing webpages will fail to identify them.
Why Traditional Methods Can’t Detect These Phishing Repositories
Anti-bot Technology – Cloudflare Turnstile
First, the threat group running this particular campaign has implemented anti-bot technology, which determines whether a visitor is human. This is important to fraudsters who want to differentiate between genuine human visitors (potential victims) or automated tools (potential cybersecurity researchers or vendors).
Legitimate websites use anti-bot technology to prevent undesirable automated activities such as web scraping or other abuse. Cloudflare offers one such anti-bot tool called Turnstile, now freely available to the public. Turnstile has reduced the hassle of using the Internet for many of us by eliminating the need to complete indecipherable CAPTCHA forms or identify all the stoplights in a set of images. Unfortunately, cybercriminals can also use this tool to their advantage.
This abuse of Turnstile by cybercriminals isn’t new, but it appears to be the first instance of its use in this context and against this specific group of financial institutions.
Anti-bot technology is an obstacle many vendors’ automated web scanners cannot overcome.
The evidence that brings us to this conclusion includes:
-
- These sites are not present in third-party phishing feeds, indicating they haven’t been identified and reported by other vendors or parties as spoofs.
-
- When discovered, these sites are still active and not blocklisted by Google Safe Browsing, anti-virus vendors, or various content delivery networks (CDN), etc. – again, indicating they’ve not been detected and reported by others
-
- Some of these phishing sites may have been active for a month or more, as indicated by dates listed in the repository directories
Despite the challenge posed by anti-bot technology in this instance, Allure Security successfully detected these sites.
Typosquat-based Detection Fails to Find These Malicious URLs
Second, online brand impersonation detection methods that rely on identifying homographs, typosquats, or misspelled domain names would overlook these malicious URLs. In some cases the root domain will include the name of a financial institution (or variation) from the impersonated group. Tools like Dnstwist or other phishing domain scanners might detect these, but only for that one financial institution whose name is in the root domain.
These detection methods focus on the root domain, and in some cases the subdomain. However, they do not consider subdirectories (e.g., “subdirectory” or the text after the slash in alluresecurity[.]com/subdirectory). This limits their effectiveness in identifying phishing attacks that deceive potential victims by making reference to an institution’s brand in a subdirectory.
Phishing Kits 101 Overview
Our threat response team is very familiar with phishing kits, having dealt with countless examples of repositories full of spoof login pages targeting multiple financial institutions over the years.
Ready-made Phishing Campaigns
Phishing kits typically include ready-made templates to allow for very quick creation of numerous phishing pages targeting numerous financial institutions at massive scale. Those templates may include graphics, code, email templates, landing pages, and anything else needed to launch phishing campaigns.
The templates will mimic the legitimate website of a financial institution and any login fields in an attempt to trick victims into giving over their usernames, passwords, email addresses, and other sensitive information. Many kits also include scripts that automate the sending of any stolen data to the attacker via email, text message, mobile app messaging or other channels. More advanced phishing kits such as CryptoChameleon can even bypass multi-factor authentication by facilitating the theft of time-based one-time passwords (TOTP).
Phishing-as-a-Service
Phishing-as-a-service (PhaaS) platforms make it even easier for fraudsters to launch phishing attacks. PhaaS will not only include a phishing kit, but also tutorials, hosting services, target lists with contact information, and more.
Phishing kits and PhaaS are a problem because of their:
-
- Ease of use – they lower the barrier to entry so that even novice attackers can launch phishing campaigns
-
- Speed – they spit out scam websites in minutes
-
- Scale – they allow for the creation of multiple unique websites targeting multiple brands very quickly
This results in an increasing number of phishing sites, targeting an increasing number of organizations. In addition, by significantly reducing the time and effort required to launch a scam, they allow for quick activation, de-activation, and relocation – further complicating the challenge of defending against such phishing threats.
Recent Spate of Phishing Page Repositories Targeting FIs Discovered by Allure Security
Below you see an small sample of the various spoofed log-in pages hosted on these recently discovered phishing site repositories:
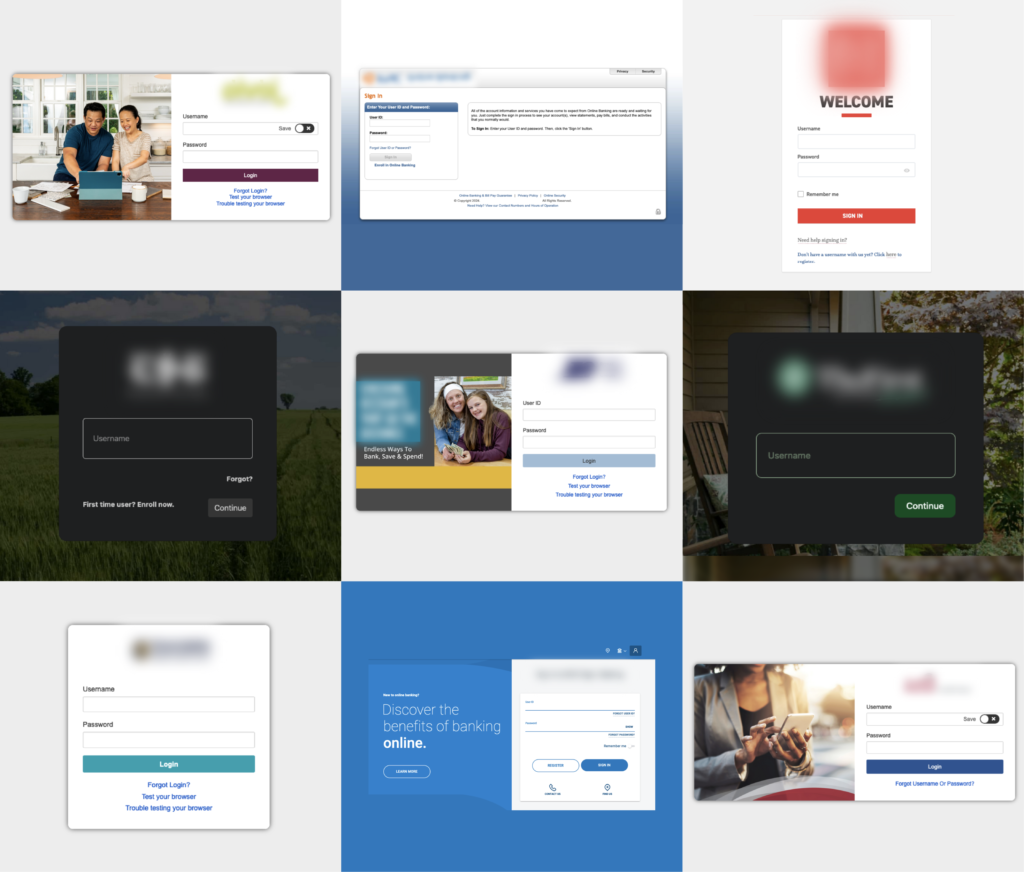
We’re discovering new examples of this particular breed of repository by the hour but have attempted to quantify the threat with the following estimates:
-
- We’ve detected 5 to 10 of these repositories each day over the past week or so
-
- The repositories typically contain 10 to 20 customized phishing kits (i.e., .zip files)
-
- The repositories typically impersonate 10 to 20 of a similar group of brands
-
- Some of the larger repositories include 30 to 40 phishing pages targeting various brands (and in some cases multiple pages targeting the same brand)
Consistent patterns we’ve observed across many of these most recent phishing repositories suggest to us that they are the work of the same group.
Some of those patterns include:
-
- Brands targeted – We’re seeing a similar set of regional bank and credit union brands targeted by each repository
-
- Top-level domains – The use of similar top-level domains (TLDs) – particularly .icu but also .support, .tech, .cloud, .online, and others (including .com)
-
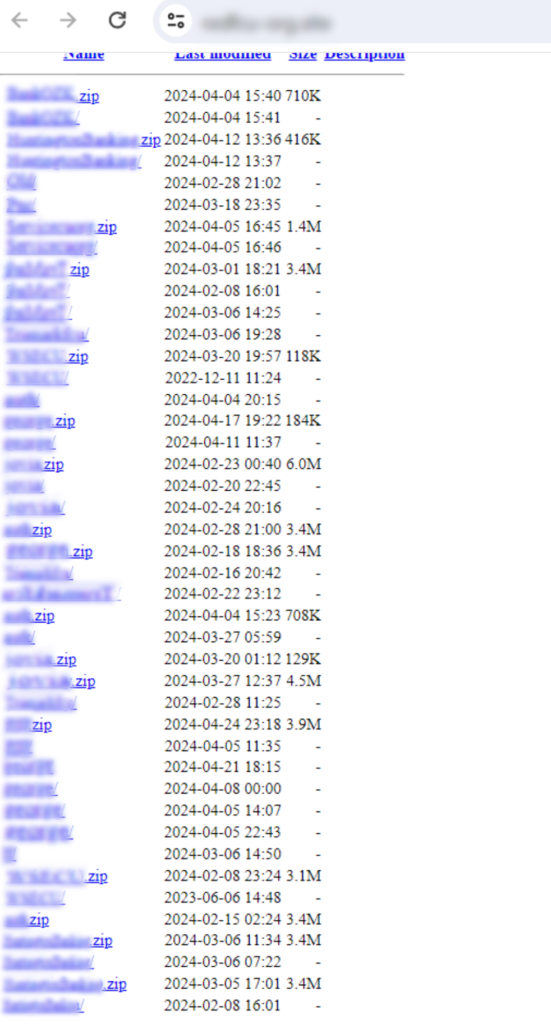
- Exposed index – The root domain’s directory is sometimes left open and subdirectories are labeled with the targeted financial institution’s name, nickname, acronym, or sometimes just random text
-
- Hosted .zip files – Along with the subdirectories are similarly named .zip files containing the code for a particular phishing page
Below you see a screenshot of the open directory of one of these phishing repositories.
Taking Action to Protect Against Increasingly Sophisticated Phishing Threats
First, if you manage your online brand protection in-house, it’s more important than ever to evaluate the effectiveness of your current strategy. Brand protection vendors are experts in keeping pace with scammers’ ever-evolving phishing tactics to ensure they can spot the scams these criminals tirelessly work to hide from the brands they impersonate. While traditional methods like identifying registered domains that use misspelled names previously offered at least a modicum of security, relying solely on these approaches is bordering on negligence these days. Your brand’s reputation and customers/members deserve better.
Second, if you do outsource your online brand protection, challenge your provider on how they handle these types of threats. As we highlighted at the beginning of this article, we believe most vendors aren’t equipped to detect scams such as these within any reasonable amount of time. Allure Security on the other hand excels at identifying and eradicating these advanced attacks before they can harm anyone. Our ability to proactively detect and shut down such scams can prevent any potential victim from ever encountering them. If you’re considering a switch or want to explore Allure Security’s offerings, do get in touch.
Related resources:
-
- Explore the elements of a mature, modern program by reading our comprehensive online brand protection guide.
-
- Review case studies in our resource center to discover how other financial institutions like you have improved the effectiveness and efficiency of their online brand protection with Allure Security.
-
- Learn about the increasing prevalence and risks of iOS 17 sideloading and alternative app stores to your mobile banking app.




