Last Updated July 18, 2024
As more people do more online, businesses that take protecting their brand seriously stand to win. Brand protection both defends a business’s reputation and protects prospects and customers against online fraud. Some consumers will blame the brand for brand abuse even if it’s somewhat out of the business’s control. People that fall victim to online brand impersonation attacks are more likely to take their business elsewhere and are less likely to engage with a brand online as they lose faith in the authenticity of these channels. This is why online brand protection is important – protecting your digital reputation reduces cybersecurity, reputation, and fraud risk. Doing online brand protection right can not only reduce risk but also reduce fraud, prevent revenue loss, increase customer satisfaction, and preserve trust in a brand.
With this article, we’ll summarize online brand protection and help you understand some of your options for protecting your brand online. Online brand protection is a team sport and so this article can benefit executive leadership, cyber security professionals, brand protection managers, legal professionals concerned with intellectual property and trademarks, and sometimes even product managers. Online brand abuse and impersonations affect nearly every industry though financial services, software-as-a-service, e-commerce/retail/apparel, and cryptocurrency are some of the top industries targeted by brand impersonation attacks.
Online brand protection or protecting your brand online consists of identifying and taking action to stop the unauthorized use of your brand name, brand logo, and brand messaging on the internet. Put another way, brand protection seeks to stop the abuse of your brand online.
Registering a trademark for your brand would qualify as brand protection because that registration gives you grounds to pursue legal action against someone that copies your brand or uses it without permission. It makes some sense then that law firms, which help businesses register trademarks, might also offer brand protection services. Unfortunately, law firms don’t typically have the brand protection software necessary to discover online brand impersonations across the entire internet. Digital brand protection tools powered by machine learning can evaluate tens-of-millions of websites every day – a team of lawyers cannot.
A brand name makes it easier for consumers to recognize and remember a business and hopefully brings along with it positive perceptions of the quality of the information, products, or services provided by that business. In other words, a brand absolutely has value because we know that we all have preferences for certain brands because we trust them and know to expect a certain quality.
Online brand protection matters because brand reputation affects consumers’ purchase decisions and therefore a business’s revenue and growth. Cox Enterprises VP and CISO David McLeod put it this way during a panel discussion, “There’s plenty of research out there that shows that revenue growth is driven by no negative sentiments.” He added, “More than the marketing plans, just by not having a tarnish on the brand is an accelerator. How do I keep the brand clean when I don’t control where the brand is being used?” For more on this topic from David, see the video in the Online Brand Protection KPIs section below.
At least a part, if not the majority, of the value of your brand is the trust you’ve built with your customers, and that’s exactly what online scammers seek to exploit. Online brand abuse or brand impersonation takes the form of fake websites, fake social media accounts, fake mobile apps, fake online ads, etc. “Fake” here means that the owner or producer of that online property is impersonating a trusted brand that they don’t have permission to use. The reason the scammers’ bother to impersonate your brand is because they can profit from its value, even if they don’t own it.
For more on different types of brand impersonation and how to identify them, see our guide to “What is Brand Impersonation?“.
Scammers make money off of exploiting your brand by using it to persuade victims to give up their credentials, payment details and more. In turn this costs you money, despite it being somewhat out of your control. It costs you in terms of lost revenue/sales, fraud, investigation and response expenses, reimbursing customers’ losses, decreased customer satisfaction, customer churn, and damage to your brand and reputation–and yes, many of these costs are intertwined and multipliers of each other.

An example of a direct tangible cost of online brand impersonations for a retailer is lost revenue. In one case, an outdoor apparel vendor found fake Facebook ads scamming hundreds of online shoppers and costing the retailer hundreds-of-thousands of dollars in revenue. Over a span of two months, the retailer lost $20,000 in revenue a day due to the deceitful Facebook advertising.
Consider some of these additional indirect costs of unsatisfactory online brand protection:
Abuse of your brand online can cost you, that’s why preventing it with brand protection matters.
The history of trademark legislation, which we’ve established is one form of brand protection, allegedly dates back to the 1300s and required bakers to brand, or put their mark on, their bread. We’ll leave that tale to the lawyers and set our sights sometime around the dawn of the world wide web as we know it today.
We might say that protecting your brand on the internet requires something to protect it against. So, homing in on some of the first examples of online brand abuse might guide us. As Allure Security CEO Josh Shaul says, “Folks have been making money on the Internet with fraud for some time. It’s kind of the oldest business on the Internet.” We could argue that a major milestone in online fraud arose with the dawn of e-commerce.
Allegedly, the first e-commerce transaction occurred in 1994 and involved the purchase of the album “Ten Summoners’ Tales” by the musician Sting. Around this time, the story goes, a rather unsophisticated fraud method consisted of miscreants entering in a stolen credit card number along with a famous person’s name (e.g., Mickey Mouse or Bill Clinton) to make a purchase online. Eventually merchants learned to validate the name associated with the payment card number, but this rather crude method did work for a bit. Note that scammers continue to impersonate celebrities to this day – Australia filed suit against Facebook for scam ads it allowed on its platform that impersonated celebrities.
Dr. Ed Amoroso, former Chief Security Officer at AT&T and current CEO of the advisory firm TAG Cyber, suggests that we could think of website defacements as some of the earliest examples of brand abuse. A website defacement consists of taking advantage of a vulnerability in a website to alter its appearance. A business’s web presence makes up a humongous part of their brand and so we can consider tampering with that a form of brand abuse. One of the first well-known examples of a website defacement occurred in 1996 when someone altered the U.S. Department of Justice’s homepage to read “Department of Injustice” and included pornographic images for good measure.
In the late 1990s, we also saw the rise of cybersquatting. Cybersquatting involves purchasing and registering domain names associated with or, in the case of typosquatting, misleadingly similar to brand names and other trademarked terms. Early on, some brands failed to take quick action to register and take control of domain names associated with their brand. Cybersquatters took advantage fast and registered those domains to then resell them at a profit to the trademark holder or by misusing them to scam consumers. Fast forward to today, some brands that don’t take action to quickly establish their presence on various social media platforms may also find themselves at the mercy of swindlers and leave their customers vulnerable.
Allure Security CEO Josh Shaul explains how businesses started to take action on cybersquatting. “When organizations started to look for these problems, they started to look for them because customers called and complained. Organizations know how to respond to that, but they wanted to get proactive so what they started to do was look for new websites that popped up that had a name similar to theirs.”
One of the earlier forms of online brand protection involved monitoring the registration status of domains, aptly named domain monitoring. Domain monitoring for brand protection use cases focuses on alerting you when domain names using your company name or similar to it are registered. Such a registration can tip you off to a potential scam. Unfortunately, this approach still requires a human to visit the suspicious site and determine whether it’s a problem.
Something else to keep in mind when thinking about protecting your brand and customers online is that enterprise email security solutions don’t protect people outside your company from phishing attacks. Customers interacting with your brand fall into this external group, meaning you can’t control their exposure to misleading links in their emails. Also, we’ve observed fraudsters using QR codes and physical mail to spread these deceptive links and bypass email spam filters.
The image below shows some traditional approaches to protecting a brand against online impersonations and their shortcomings. Long-story short, legacy approaches have steadily decreasing effectiveness against fraudsters’ continuing innovations, and, those legacy approaches are also typically too expensive these days.
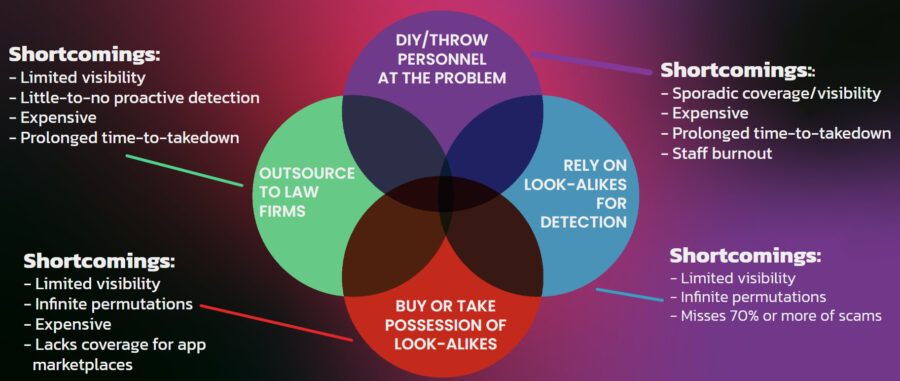
The problem is there are too many sites, millions of them. In addition, attackers have evolved beyond using misspelled brand names. A phishing study conducted by researchers from Arizona State University, Google, PayPal and Samsung found that traditional domain monitoring fails to identify 71% of malicious websites. Domain monitoring alone is no longer effective in detecting online brand impersonation attacks.
Phishing-as-a-service platforms have also made it easier for even amateur fraudsters to develop and launch phishing campaigns in minutes. Read more about an Allure Security discovery of a surge in phishing kits targeting regional banks and credit unions in 2024.
A key aspect of digital brand protection is reducing the risk of someone abusing your brand online. The first step towards that objective requires you to establish control of your brand online to the extent possible. Here are some things to be sure you take care of if you haven’t already.
Read more about these tips, tailored to regional banks and credit unions, in our article “Protecting Regional Bank & Credit Union Brands Online.”
Protecting your brand online of course also extends beyond finding and taking down spoof websites that impersonate your brand.
You also need to monitor for:
We’ve observed a marked increase in the number of rogue mobile apps using our customers’ brands published on alternative app stores (i.e., marketplaces other than the official Apple App Store or Google Play Store) over the past couple of years. In the past, rogue Android apps were more prevalent. However we expect to see an increase in rogue iOS apps and more alternative iOS app marketplaces coming online as a result of Apple beginning to allow users in Europe to sideload apps to their devices beginning in March 2024.
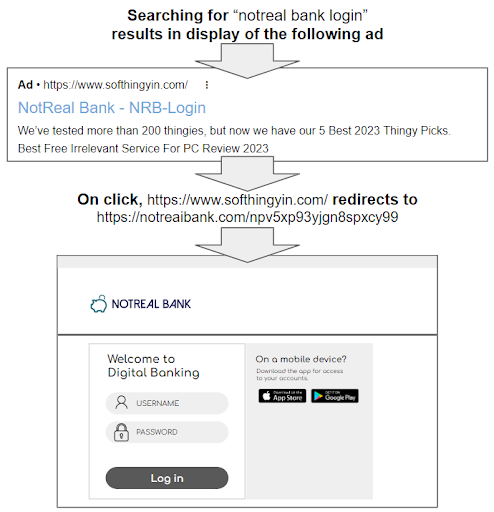
At Allure Security, we’ve helped customers identify and mitigate a wide variety of online brand impersonations across online marketplaces, digital advertising, social media, mobile app marketplaces, and more.
Our blog offers a number of tips for protecting your brand in the following areas:
In the realm of online brand protection, a growing concern is the impersonation of executives and staff on social media. This type of fraud involves creating fake social media profiles that mimic your team members, particularly on platforms like LinkedIn, Twitter, Facebook, and others. Under the guise of being trusted brand representatives, these imposters often lure other users with false promises of substantial discounts or investment opportunities.
The ever-growing nature of social media content necessitates robust, automated monitoring systems to detect and mitigate the misuse of your employees’ identities. Without such measures, the sheer volume of content makes satisfactory coverage unattainable.
Moreover, for executives reluctant or uninterested in maintaining a social media presence, proactive account registration is crucial. This preemptive step not only thwarts unauthorized individuals from claiming such profiles but also streamlines the process of removing fraudulent accounts by referencing these official profiles.
For deeper insights into safeguarding leaders without a digital footprint, explore our blog: protecting company leaders that lack an online presence.
The number of unique scam websites used in brand impersonation attacks hit an all-time high recently according to the Anti-Phishing Working Group. The problem continues to grow, so it’s increasingly likely that you may find a fake website impersonating your brand and targeting your customers. So what do you do if you find one?
If you don’t specialize in online brand protection, you’re typically better off choosing a brand protection-as-a-service vendor. Vendors typically use AI-powered technology to more thoroughly scrutinize the internet for brand impersonations and apply more effective, repeatable response methods. However, if you should choose to try and takedown a website on your own, here’s an overview of the steps you ought to take.
An internal team may have deployed the site without your knowledge. Or the site may belong to an authorized reseller, partner, or agent. If the site turns out to be authorized, identifying it is still of value as it helps you establish an inventory of authorized web properties.
Does the site seek to defraud by stealing your customers’ or employees’ credentials, payment card information or other data? Or is the site infringing on trademarks for instance by selling counterfeit goods? While you’ll follow a similar process either way, there are some nuances in following up on each type of case. For example, Google may blocklist a site engaging in fraud but be less likely to block a site that’s infringing on a trademark.
Report the problem site to Google, Microsoft, the Federal Trade Commission, and the FBI’s Internet Crime Complaint Center (IC3). Understand that reporting the site to Google, Microsoft, etc. does not guarantee that those organizations will take immediate, or any, action. Vendors such as Allure Security have built trust with many of these organizations which can help expedite such actions.
Use Whois Domain Lookup to find out where you’ll need to send your takedown request. Note that in many cases the hosting provider or registrar may not respond to your request.
You will need to grab screenshots of the scam website along with a list of the problem URLs. You will also need to gather together corresponding screenshots and URLs for your authentic web pages. Vendors such as Allure Security can save you time in this process by automating the creation of these evidence packages. Many law firms also offer such services – though because they typically bill by the hour it’s not always the most cost-effective option and is by its nature a “whack-a-mole” approach that reacts to scams after they’ve already done damage. Using a vendor can help you take a more proactive approach.
Creating a takedown request is no small feat. The Internet Corporation for Assigned Names and Numbers (ICANN) provides a thorough guide for preparing domain name takedowns.
You will need to research the host’s or registrar’s reporting mechanisms. Many times their abuse reporting processes differ for fraud sites versus trademark abuse as mentioned in step 2 above. Searching the name of the host or registrar along with “abuse” should help you locate instructions. If you can’t find abuse policies or guidance on their website, many hosts and registrars have an “abuse@[host or registrar domain]” email address if you can’t find specific guidance on the websites for submissions. PRO TIP: Use local language. Not everyone can read English. Google Translate can help.
Many times it can take multiple requests before a host or registrar will take action, if they respond at all. If you don’t receive a response after a reasonable amount of time, you can file a complaint with ICANN (see their Contractual Compliance help center for guidance). It’s a lengthy process but can help get results even in seemingly hopeless situations.
If you think the website takedown process sounds time-consuming and complicated, you’re right. Luckily, brand protection-as-a-service vendors like Allure Security have streamlined these processes and through repetition built relationships with many of the stakeholders to get results more quickly.
A brand protection strategy goes beyond simply a collection of tactics. Many organizations want to take a more proactive approach to abuse of their brand online. At the risk of oversimplifying, that mostly means not simply waiting until customers call to complain about falling victim. It’s actually possible to find the origins of an online scam before a single one of your customers’ falls victim and without sinking an enormous amount of time, effort, and money into manual web searches.
Because this is a guide for busy people, we won’t walk through the entire strategic planning process here, though we will offer a few hints. We’ll define a strategy as a plan to achieve a longer term goal. Such a plan essentially consists of documenting your current state, your desired state, the plan to get from the current state to the desired state and then how you will measure your progress over time.
Many of our customers come to us because while they have some processes in place, they still miss instances of fraud. Usually, they learn of a scam they missed because customers have called in to the call center to complain about having been scammed. Many organizations will have a domain monitoring vendor in place or have built an internal process using a free phishing domain scanner such as dnstwist.it.
Monitoring for permutations of a domain name is a start and better than nothing. However, as stated on the dnstwist GitHub page:
“It’s mathematically impossible to check all domain permutations – especially for longer input domains which would require millions of DNS lookups. For this reason, this tool generates and checks domains very close to the original one. Theoretically, these are the most attractive domains from the attacker’s point of view. However, be aware that the imagination of the aggressors is unlimited.”
In addition, attackers have moved beyond simple typo- or cyber-squatting. Cybersquatting uses misleading permutations of a domain name to trick visitors into believing a website is an official channel. A phishing study conducted by researchers from Arizona State University, Google, PayPal and Samsung found that traditional domain monitoring fails to identify 71% of malicious websites. More recent research on the topic from Allure Security finds that relying solely on domain-name permutations misses 87% of impersonations of retail and other consumer facing brands and 94% of impersonations of credit union brands (for more see our SPOOF23: Retail and SPOOF23: Credit Unions reports). Alone, DNS and domain monitoring are no longer reliable ways to detect brand impersonations and phishing.
Depending on your brand protection program’s maturity, you may need to begin with some of the tips outlined in the “Getting Started” section.
At the least, you will need to:
Hoping to find more scam sites before their customers have fallen victim is one of the top reasons business’s approach Allure Security for online brand protection. One brand came to us with the specific goal of gaining a “…proactive edge on the bad guys.” The publishing of a fake website impersonating a brand can be the first sign of a phishing scheme in development. After that the scammer launches their phishing campaign by choosing their distribution channel (e.g., e-mail, text message, QR code) to send a link to the site to their targets. To the brand seeking a proactive edge, finding these sites in their beginning stages, prior to the launch of a phishing scam for example, was their desired state. An additional advanced measure that contributes to a proactive strategy incorporates adding a virtual watermark to digital content that “phones home” when it’s reproduced.
Perhaps obviously, customers serving as a detection system for online scams won’t get you ahead of the brand damage, fraud losses, and lost revenue that stems from online brand abuse. Simply playing more rounds of reactive “whack-a-mole” in terms of knocking down websites as they’re reported by customers also isn’t exactly a progression.
So how will you get ahead? Vendors such as Allure Security apply artificial intelligence to the problem to find more fake websites, deceptive social media accounts, and rogue and malicious mobile apps than traditional approaches. Allure Security’s AI-powered detection engine, for example, automates the assessment of more than 50 million websites a day (a number which increases every month). This is a scale that a team of humans, no matter how skilled, cannot achieve. Best of all, this power allows vendors like Allure Security to find scams in their beginning stages – i.e., during development and testing or quickly after deployment and before any person has visited them. Allure Security, for example, shortens the life cycle of scams online.
All of this is to say that truly proactive and effective online brand protection goes beyond website takedowns. Proactive brand protection reduces reputation risk, protects revenue, and increases customer satisfaction, loyalty, and trust. Achieving more cost efficiency is also an admirable goal.
We can’t necessarily prescribe the best KPIs for your situation as it depends on your brand’s specific goals. Enforcement action metrics will likely make up part of how you measure progress, but don’t lose sight of the impact brand protection can have on the bottom line (e.g., revenue protected, reputation risk reduced, etc.).
As you work with your team and internal stakeholders, consider the following non-exhaustive list of questions to help decide the best KPIs for your program:
In the video below, Cox Enterprises VP and CISO David McLeod offers some ideas for quantifying the effectiveness of your brand protection efforts:
Renowned branding expert and author Marty Neumeier states, “Your brand isn’t what you say it is. It’s what they say it is.” Essentially, that means you don’t control all aspects of your brand. As David McLeod mentioned above, that can be especially challenging online where you don’t always control the use of your brand.
A strong brand attracts and retains customers. It’s one of your most valuable assets – valued both by you and your customers. Protecting your reputation and managing associated risks clearly contribute to the bottom line and is a high stakes endeavor. You’ve built trust with your customers and in turn they expect you’re doing what you can to ensure the safety of their interactions with you.
You need to do your due diligence as well as build and maintain an online brand protection monitoring strategy that allows you to proactively gain visibility into the use of your brand online (whether authorized or not) and quickly respond to misuse as soon as possible. As we’ve covered, that comprises:
Finally, thank you for reading this guide. It shows you’re taking a step toward improving your brand security. And, if you think about it, when you protect your brand you help make the world a better place. Yes, of course there are commercial interests at play too, but you’re also doing your part to help protect you, your family, us, our families, and the public at large against fraud and the harm it does to all of our economic and emotional security.
Solution Pages
Quick Links
Copyright © 2024 All rights reserved.