Table of Contents
Distinguishing brand impersonations in the world of X/Twitter can sometimes be perplexing. Unlike LinkedIn, which enforces more stringent measures against misrepresentation, X tends to take a more flexible stance. This has made it harder than ever to know what’s authentic or not on X. This complicates identification, reporting, and takedown of online brand impersonations on the platform.
Leading financial institutions and retailers trust our best-in-class takedown team to efficiently and efficiently stamp out X impersonations. So, we spoke with them to write this article explaining the subtleties of X rules regarding brand, executive, and employee impersonations and providing guidance for reporting violations and managing takedowns.
Defining X and Twitter Impersonations: Misleading and Deceptive Identities
The first part of battling impersonations of your brand or employees on X is understanding X’s definitions about what does and does not constitute an impersonation.
Here’s how X defines impersonation and deceptive identities in its current misleading and deceptive identities policy:
-
- Impersonation – You may not pose as an existing person, group, or organization to mislead others about who you are or who you represent. Accounts that violate this policy will misrepresent their identity by using at least two elements of another identity, such as the name, image, or false claims of affiliation with another individual or organization in their profile or posts.
-
- Deceptive Identities – You may not pose as someone who doesn’t exist to mislead others about who you are or who you represent. This includes using at least one element of someone else’s identity on your profile or posts in a misleading way, such as using another individual’s image or making a false statement of affiliation with an existing individual or entity. We also consider accounts to be deceptive if they use a computer generated image of a person to pose as someone who doesn’t exist.
You’ll notice X’s emphasis of “at least two elements” in the definition of impersonation. The same policy states, “Accounts that share your name but have no other commonalities are not in violation of this policy.” X considers parodies, social commentary, and fan accounts to be an acceptable part of its ecosystem. Granted, X also requires that such accounts “clearly indicate that the account is not affiliated with the subject portrayed in the profile” in their account name and bio.
Even if only slightly, this differs from other social media platforms – such as Linkedin’s stand on fake profiles where inaccurate information is strictly prohibited.
Experts on our takedown team find that even though X’s policy requires “at least two elements” of another account’s identity to qualify as an impersonation, accounts that do not have a profile picture at all or do not have a picture that matches the impersonated account’s profile picture are not typically prioritized for takedown.
X and Twitter Takedown Guidance
Reporting trademark issues on X is about safeguarding the unique words, symbols, or designs that customers recognize as identifying your products or services. Reporting copyright violations is about protecting your creative work. Trademark complaints relate to the unauthorized use of your brand’s logo, name, etc. Copyright complaints focus on the use of your unique creations (e.g., writings or pictures) without your permission.
Both trademark and copyright complaints differ from reporting impersonations which involve content aimed at tricking others by pretending to be you or your brand. Knowing these differences helps you report problems more effectively on X. We cover reporting each of these types of issues below.
Requesting Trademark Infringement & Copyright Violations Takedowns on X/Twitter
There may be instances where a post infringes on your brand’s intellectual property rights, in which case X’s “rule of two” impersonating elements is not necessarily required to justify removal.
X has different reporting requirements for trademark infringements vs. copyright violations. It’s important to understand the difference to avoid any delay in enforcement actions:
-
- Trademark infringement typically relates to the unauthorized use of a brand’s identifiers such as logos, brand names, or product names
-
- Copyright violation typically relates to the unauthorized use of original creative works such as text, images, music, videos, software code, and more
Reporting Trademark Infringement
According to X’s trademark policy, “Using another’s trademark in a way that may mislead or confuse people about your affiliation may be a violation of our trademark policy.” Considering fair use of trademarks, referencing another’s trademark is not always a violation – for example, if the reference is used outside the scope of the trademark’s registration, or if its use could be considered fair use.
If you decide your brand’s trademark is indeed being infringed upon, you can report it using X’s trademark infringement form. You will need to prove that you are the trademark owner or an authorized representative of the trademark owner and provide:
-
- Your contact information
-
- Information about the account you’re reporting
-
- Evidence that you’re an authorized representative of the trademark holder
-
- The trademark holder’s contact information
-
- Information about the trademark itself
Reporting Copyright Violations
X’s fair use policy states “Certain uses of copyrighted material may not require the copyright owner’s permission.” Fair use is not an X policy but rather a matter of formal copyright law. Whether or not an instance is considered fair use is dependent on four factors:
-
- The purpose and character of the use – What is the reason that the copyrighted material is being used? Uses considered commercial are more likely to be flagged in violation of free use. Uses that add something to the original work (commentary, criticism, etc.) are likely to be considered fair use.
-
- The nature of the copied work – Is the copied work factual (the record of a historical event) or fictional (a popular movie, book, etc.)? The use of factual works weighs in favor of fair use, whereas the use of fictional works weighs in favor of violating fair use.
-
- The amount and substantiality of the copied work – How much of the protected work was used? The more that a work is copied, the less likely it is to be considered fair use. Shorter excerpts are more likely to be considered fair use.
-
- The effect on the copied work’s value – Could the use in question have a negative effect on the work’s value? If the copying might bring harm to the work’s market (i.e., creating a substitute or replacement for the work) then it is likely not fair use.
If you believe an X account is violating your copyrights, file a copyright infringement report here. Note that X will initiate the process by notifying the alleged violator on your behalf. The reporting form requires the following information:
-
- Contact information for you and the copyright holder
-
- Details about where the violating material is located
-
- The type of copyrighted work, a description of the work, and links to the work (if applicable)
-
- Link(s) to the infringing material
-
- Opting into “acknowledgment,” “good faith,” and “authority to act” statements
-
- E-signature
Requesting Impersonation Takedown on X/Twitter
You may find impersonations of your brand on X profiles, posts, lists, moments, products, ads, and direct messages. Submitting reports for each type of impersonation follows a common format. Below we highlight some of the nuances of the different reporting types.
Requesting X/Twitter Impersonation Takedowns Directly from Profiles, Posts, Lists, or Moments
Reporting or requesting a takedown directly from a profile, post, list or Moment all follow a similar set of actions as illustrated in the diagram below.
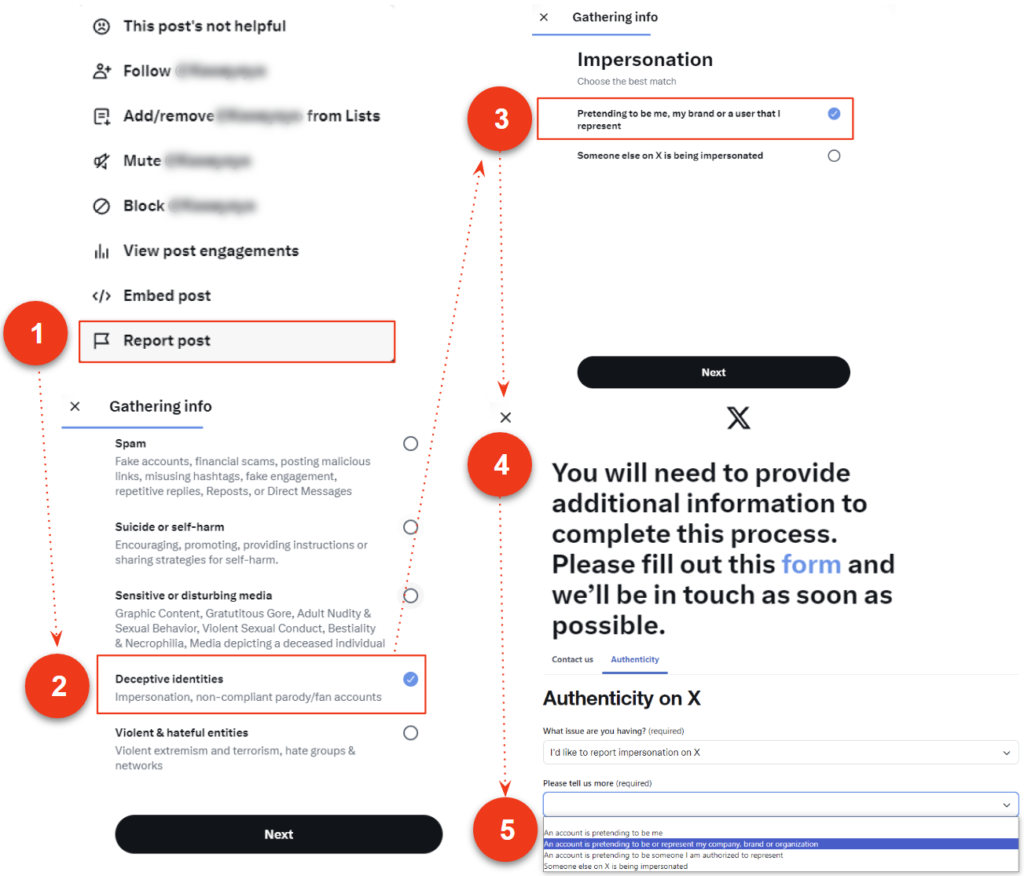
Reporting a brand impersonation will prompt you to fill out this form. After confirming your identity, you will be asked to provide company information, personal information (name, relation to company), and information about the account you’re reporting.
Reporting Profiles
-
- Open the profile you’d like to report.
- Select the More icon
.
- Select Report and then select the type of issue you’d like to report.
- X will include the text of the posts you reported in follow-up emails and notifications. To opt out of receiving this information, uncheck the box next to Updates about this report can show these posts.
- Once you’ve submitted your report, X will provide recommendations for additional actions you can take to improve your experience.
Reporting Posts
-
- Navigate to the post you’d like to report.
- Click or tap the More
icon located at the top of the post.
- Select Report post and follow through the steps pictured above to provide the required information.
Reporting Lists
-
- Lists can be reported from the detail page of a List, or from the Notifications tab.
- Navigate to the List you’d like to report.
- Click or tap the More
icon at the top of the List.
- Select Report List and follow through the steps pictured above to provide the required information.
Reporting Moments
-
- Navigate to the post within the Moment that you’d like to report.
- Click or tap the More
icon.
- Click or tap Report post.
- Choose the type of issue you’d like to report.
- Once you’ve submitted your report, X will provide recommendations for actions you can take to improve your experience.
Requesting X/Twitter Impersonation Takedowns for Shop Spotlight Products, Ads, Direct Messages (DMs)
Below we explain how to report and request the takedown of offending content in a profile’s Shop Spotlight, ads, and direct messages.
Reporting Products in Shop Spotlight
It is important to note that reporting products on a profile’s Shop Spotlight can only be done via the mobile app (iOS/Android)
-
- While on a merchant’s profile, find the Shop Spotlight.
- Select the More
icon on the product you wish to report.
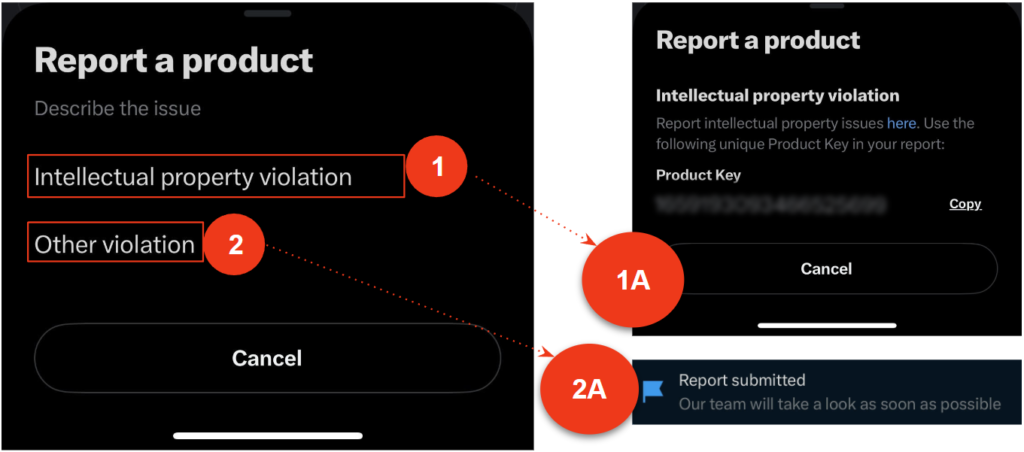
- Select Report product.
- Select Intellectual property violation (1 & 1A on the diagram below) if you’re reporting a product for issues with intellectual property rights. You’ll need to include the product ID. You can also submit an intellectual property violation directly here.
- Select Other violation (2 & 2A on the diagram) if you’re reporting a product for a different reason.
Reporting Ads
-
- Click the
icon near the offending advertisement.
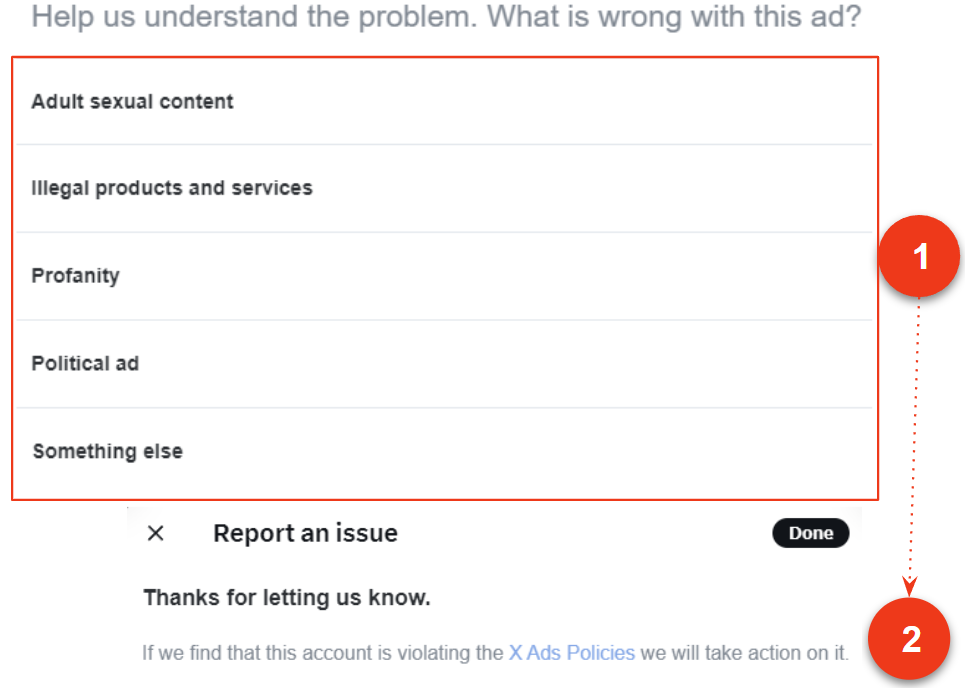
- Select Report ad.
- Select the offense from this list.
- For brand impersonations, select “illegal products and services” if applicable. If not, select “something else.”
- Selecting any offense will submit your report.
- Click the
Reporting Direct Messages
In a conversation:
- On a desktop, click on the Direct Message conversation you’d like to report.
- For IOS, swipe left on the message conversation you’d like to flag.
- For Android, tap and long-press the message conversation you’d like to flag.
- On desktop, click the More icon
- For IOS, Tap the report icon
- For Android, Tap Report conversation.
- For IOS, Tap the report icon
- Select Report @username.
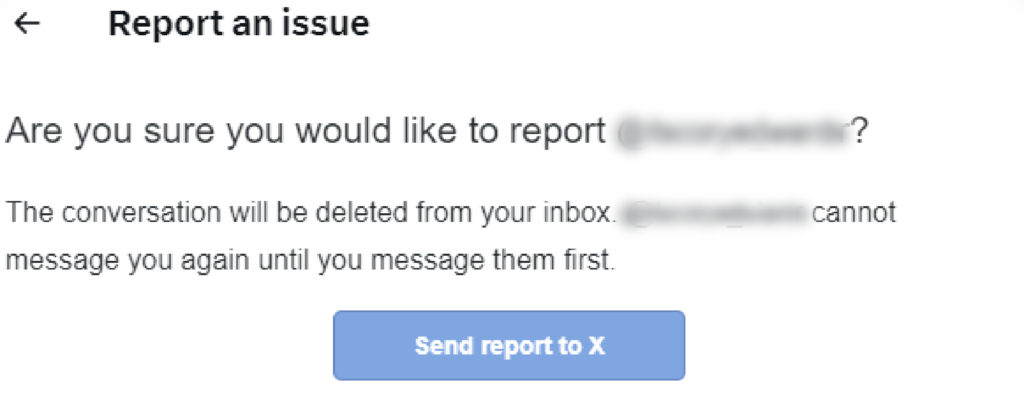
- You will be prompted to report the message for being spam or abusive or harmful.
- Reporting as spam will automatically submit a report to X, and remove the message from your inbox.
Reporting as spam will automatically submit a report to X, and remove the message from your inbox.
If you select “It’s abusive or harmful,” X will ask you to provide additional information about the issue you’re reporting. They may also ask you to select additional messages from the account you’re reporting so they have better context to evaluate your report.
The reporting process will look like this:
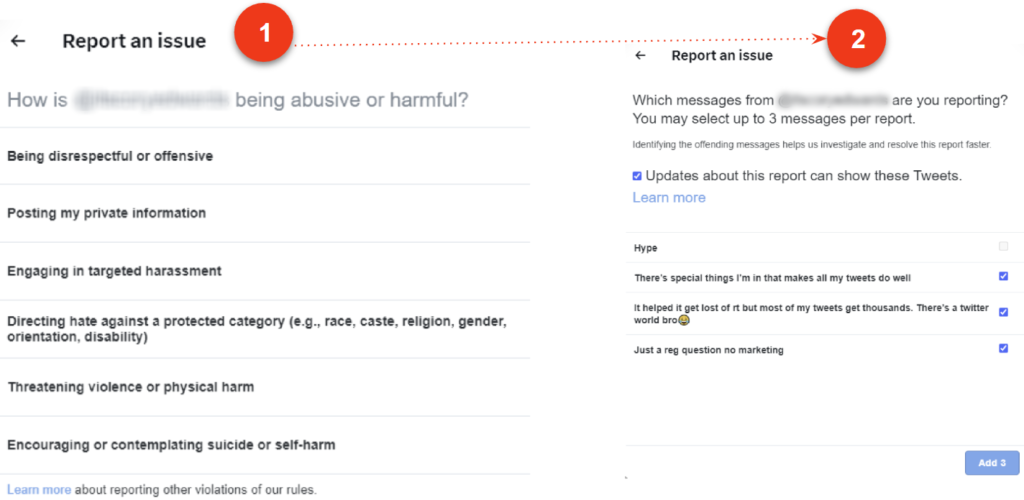
Once you’ve submitted your report, X will provide recommendations for additional actions you can take to improve your experience. You also have the option of reporting an entire conversation from a group message.
Additional actions are also available after a report is submitted, such as muting or blocking the offending profile directly from a direct message report.
WHAT YOU SHOULD DO NEXT
-
- To take back control of your brand on social media, learn more about our social media protection services and contact us.
- Read our blog post about removing brand impersonations from LinkedIn
- Review more best practices for defending your brand online with our free Busy Person’s Guide to Online Brand Protection.




