BANKING CASE STUDY – CUSTOMERS TRUST THEIR FINANCIAL INSTITUTION TO PROTECT THEM
A REAL STORY ABOUT HOW A PHISHED SITE ALMOST DESTROYED A BANK’S BRAND REPUTATION AND ATTEMPTED TO STEAL CUSTOMER PERSONAL INFORMATION
Allure Security was able to stop the damage to the company’s brand and to the trust of their customers
Allure Security was introduced to a regional bank with about $30 billion in assets, making them one of the top 60 banks in the United States. Like all banks with retail customers, they have an online portal for customers to manage their accounts and take advantage of an array of services the bank offers. Like most customer-facing websites, this bank’s customer portal is an attractive target for hackers in their quest to pilfer funds from individual accounts. To protect their customers and the bank’s reputation, its security operations team deploys an array of security measures to protect their online presence. But it was not enough.
One critical component in the system is outside of the bank’s control—their customers. While employees’ devices routinely protected by endpoint security solutions and bank employees undergo regular security training, neither of these defense techniques can apply to their retail customers. As stated in the 2019 Verizon Data Breach Investigations Report:
There is little that financial organizations can do to ensure that their customers are running up-to-date malware defenses or make them ‘phish-proof’.
For the bank, phishing attacks against their customers were a growing problem. In just one month, hackers had copied the bank’s website five times to different URLs, then sent customers phishing emails intending to lure them into revealing their credentials on these fake sites. The bank employed a domain monitoring service to identify similar-looking website names, and this approach eventually caught four of the fake sites. The fifth one, however, was reported by a retail customer, which was embarrassing for the bank. Furthermore, some of the other spoof sites had been active for days, and banking personnel had no idea how many customers might have entered their credentials, resulting in compromised accounts. They were flying blind.
Security staff at the bank realized at this point that they needed a better solution—one that could:
- Detect fake or “spoof” sites even when the URL didn’t look like the bank’s own domain
- Improve time-to-detection of spoof sites—especially important given that 70% of credentials are collected within the first hour of an attack*
- Provide greater insight regarding how many customers were impacted, and who they were
The answer was a solution from Allure Security. Working with the Allure Security onboarding team, the bank deployed Allure Security’s unique website beacons to their site—a process that took them only a couple hours. As soon as they were deployed, the bank’s security team had constant insight into accesses to their pages, whether those were deployed on the proper servers or illegally copied to a separate location as the start of a phishing campaign.
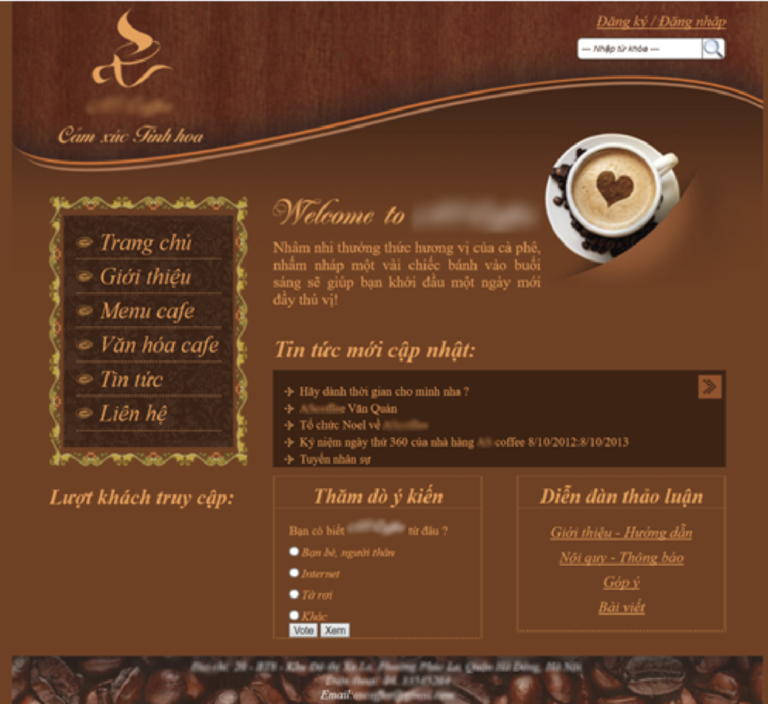
Shortly thereafter came the payoff. Allure Security’s website beacons alerted the bank security team that a copy of their site was being hosted in the most unexpected place—a subfolder on the website of a Vietnamese coffee shop! Everything looked fine on the main page. There was a photo of a delicious-looking cup of latte, and a menu (in Vietnamese). But in an obscure subfolder on the site, accessible by the correct URL, was a complete copy of the bank’s website.
Surprising—but not astonishing. As the 2019 Webroot Threat Report says:
URL obfuscation is frequently used to direct users to a malicious site, or to malicious content on a benign site. A massive 40% of malicious URLs were found on good domains, since legitimate websites are frequently compromised to host malicious content.
Hackers had broken into the site using a known vulnerability, deployed the pages, and added code to intercept customer credentials. The bank’s domain monitoring service didn’t detect this activity—and how would they?
Fortunately, Allure Security’s active approach to monitoring, using website beacons, alerted the bank’s team in seconds, letting them validate the fake and begin the takedown process. Allure Security’s solution also tracked every access to the fake site. The bank’s team was able to see the first accesses, which came from Nigeria—clearly the hacker testing out the site. Soon the site was taken down before any of the bank’s customers were impacted. And the bank’s team gathered valuable intelligence on the hacker.
This bank—and other organizations that care about protecting their customers and their brand—are facing an unprecedented challenge in detecting and stopping fraudulent websites. Only an active solution—the Allure Security solution—is up to the task.
One critical component in the system is outside of the bank’s control—their customers. While employees’ devices routinely protected by endpoint security solutions and bank employees undergo regular security training, neither of these defense techniques can apply to their retail customers. As stated in the 2019 Verizon Data Breach Investigations Report:
There is little that financial organizations can do to ensure that their customers are running up-to-date malware defenses or make them ‘phish-proof’.
For the bank, phishing attacks against their customers were a growing problem. In just one month, hackers had copied the bank’s website five times to different URLs, then sent customers phishing emails intending to lure them into revealing their credentials on these fake sites. The bank employed a domain monitoring service to identify similar-looking website names, and this approach eventually caught four of the fake sites. The fifth one, however, was reported by a retail customer, which was embarrassing for the bank. Furthermore, some of the other spoof sites had been active for days, and banking personnel had no idea how many customers might have entered their credentials, resulting in compromised accounts. They were flying blind.
Security staff at the bank realized at this point that they needed a better solution—one that could:
- Detect fake or “spoof” sites even when the URL didn’t look like the bank’s own domain
- Improve time-to-detection of spoof sites—especially important given that 70% of credentials are collected within the first hour of an attack*
- Provide greater insight regarding how many customers were impacted, and who they were
The answer was a solution from Allure Security. Working with the Allure Security onboarding team, the bank deployed Allure Security’s unique website beacons to their site—a process that took them only a couple hours. As soon as they were deployed, the bank’s security team had constant insight into accesses to their pages, whether those were deployed on the proper servers or illegally copied to a separate location as the start of a phishing campaign.
Shortly thereafter came the payoff. Allure Security’s website beacons alerted the bank security team that a copy of their site was being hosted in the most unexpected place—a subfolder on the website of a Vietnamese coffee shop! Everything looked fine on the main page. There was a photo of a delicious-looking cup of latte, and a menu (in Vietnamese). But in an obscure subfolder on the site, accessible by the correct URL, was a complete copy of the bank’s website.
LEARN MORE ABOUT HOW WE PROTECT YOUR CUSTOMERS
We’re here to answer any questions you have about how we prevent brand abuse on the web, social media platforms, and mobile app stores via site takedown, trademark enforcement, and DMCA enforcement.